Case Study: GitHub Actions, Terraform and GitOps
Project goal
Create an AWS environment with Terraform that deploys a Python application. Manage the infrastructure in Git with Terraform and automate the deployments. The client used GitHub.
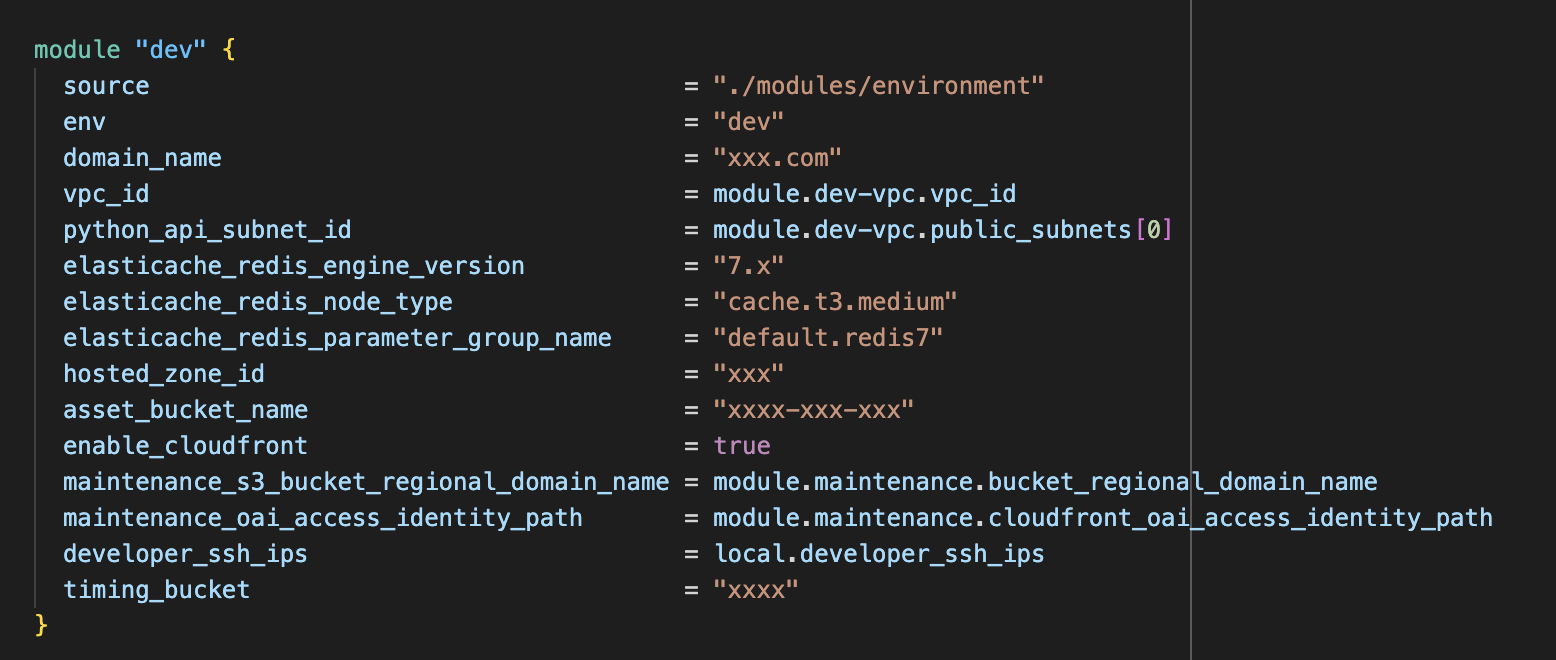
Manging an entire environment with Terraform modules
Skills and technologies used
- AWS
- IaaC
- Terraform
- AWS Security Hub
- CI/CD
- GitHub
- GitHub Actions
Solution
As the client already used GitHub, using GitHub Actions to manage infrastructure and application changes made perfect sense.
We set it up to use Pull Requests, perform code linting and unit tests on the branch, and then deploy on merging to three branches: dev for the development environment, stage for the staging environment and main for the production environment.
We used GitHub Actions to deploy both the infrastructure and the application repositories.
When someone created a Pull Request for the infrastructure repository, GitHub Actions automatically ran a terraform plan. It then stored the resulting plan in an S3 bucket ready for Terraform to apply those changes when someone approved the Pull Request and merged it into the dev, staging or main branches.
We managed differences between the environments and other credentials securely using GitHub Action Secrets, and the AWS environments used AWS Organisations to separate the dev, staging and production environments
GitHub Actions also managed code deployments, running unit tests and static code analysis for every push and deploying when pull requests were approved.
We fully configured the infrastructure to comply with CIS 1.4 and set up AWS Security Hub to monitor compliance.
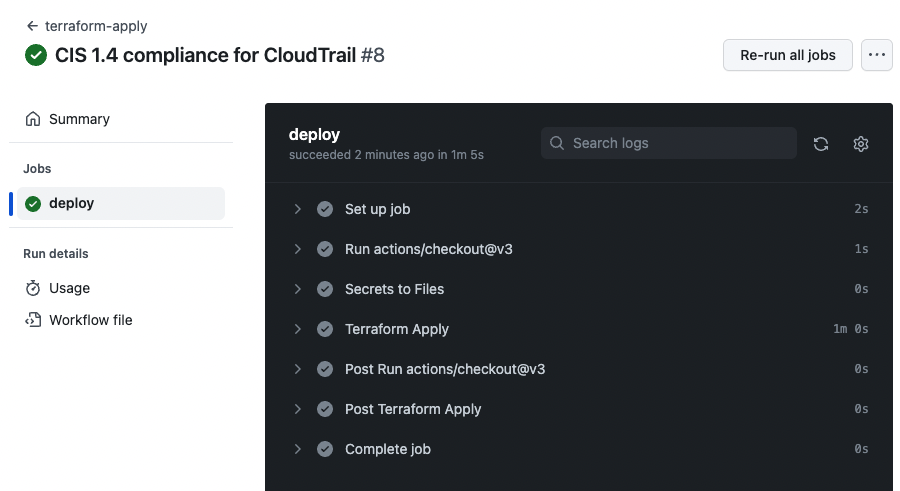
CIS 1.4 complaince infrastructure changes being applied
