Case Study: GitLab CI/CD managing infrastructure with Terraform
Project goal
The organisation already used GitLab to deploy their code and used Terraform with engineers running it on their workstations. They wanted to automate it completely.
The Terraform code sets up an Amazon ECS Fargate application and its dependencies.
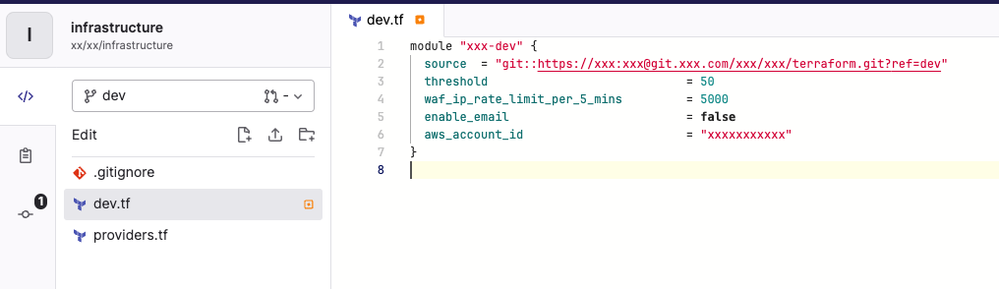
Example of using the Terraform repository in a branch
Skills and technologies used
- AWS
- Amazon ECS Fargate
- GitLab
- Terraform
- CI/CD
- GitOps
Solution
As they were already using GitLab, it made perfect sense to manage their infrastructure with GitLab. We set up the GitLab pipeline to store the Terraform remote state using the GitLab HTTP API. There were various environments, e.g. dev, staging and production, inside different AWS accounts using AWS Organisations.
The dev and staging environments are automatically shut down outside working hours and automatically restored each working day to save AWS costs.
We configured the pipeline to run tflint to validate each commit. Due to change management compliance requirements and the requirement to automatically shut down the environments at the end of the day, we used Git tags to version the terraform code repository and, in a separate infrastructure repository, used the Terraform code repository with its code included as modules with relevant configuration defined in a branch for each environment.
When the environment was to be deployed, the Terraform plan was stored using the GitLab HTTP API and a manual approval step was placed in the pipeline, allowing review of the changes that would be applied. If approved, Terraform automatically applies the planned infrastructure changes.
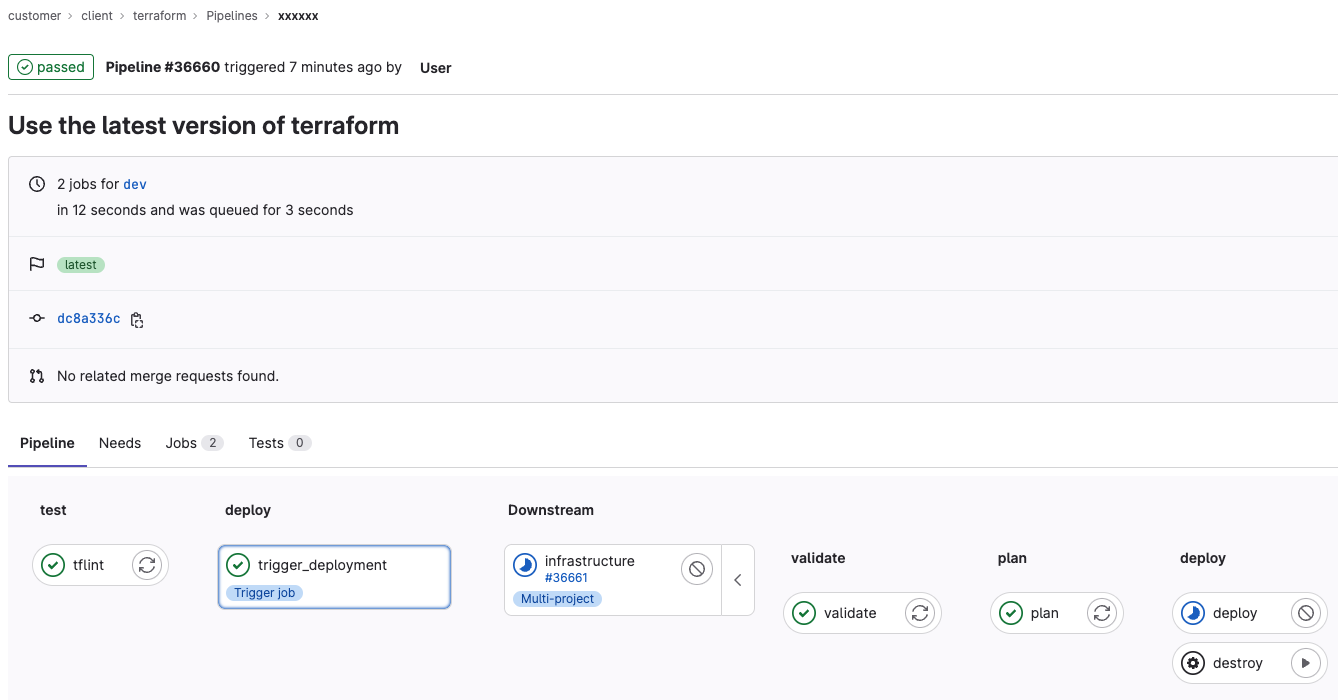
The pipeline running completing Terraform changes
